360 Cyber-wide Digital Security Brain, Overcoming the "Invisible" Security Risk Problem
2022-10-13
Digitalization is faced with dual security challenges, both internal and external, and risks are pervasive in all scenarios. Perceiving the network security situation is the most basic and fundamental work. "Seeing",as the core of security system construction, is the premise of disposal and response. Through 17 years of accumulation and precipitation, 360 has condensed into the 360 Cyber-Wide Digital Security Brain, and constantly overcome the problem of "invisible" risks in the digital security industry.
Three Cores Converge in 360 Cyber-wide Digital Security Brain
360 spent nearly 20 years, invested 20 billion, gathered more than 2,000 security experts, accumulated 2,000PB of security big data, built a security operation service system centered on "Seeing + Handling" around 360 Cyber-Wide Digital Security Brain, and formed a strong ability to "see" the cyber-wide situation and "see" advanced threat attacks.
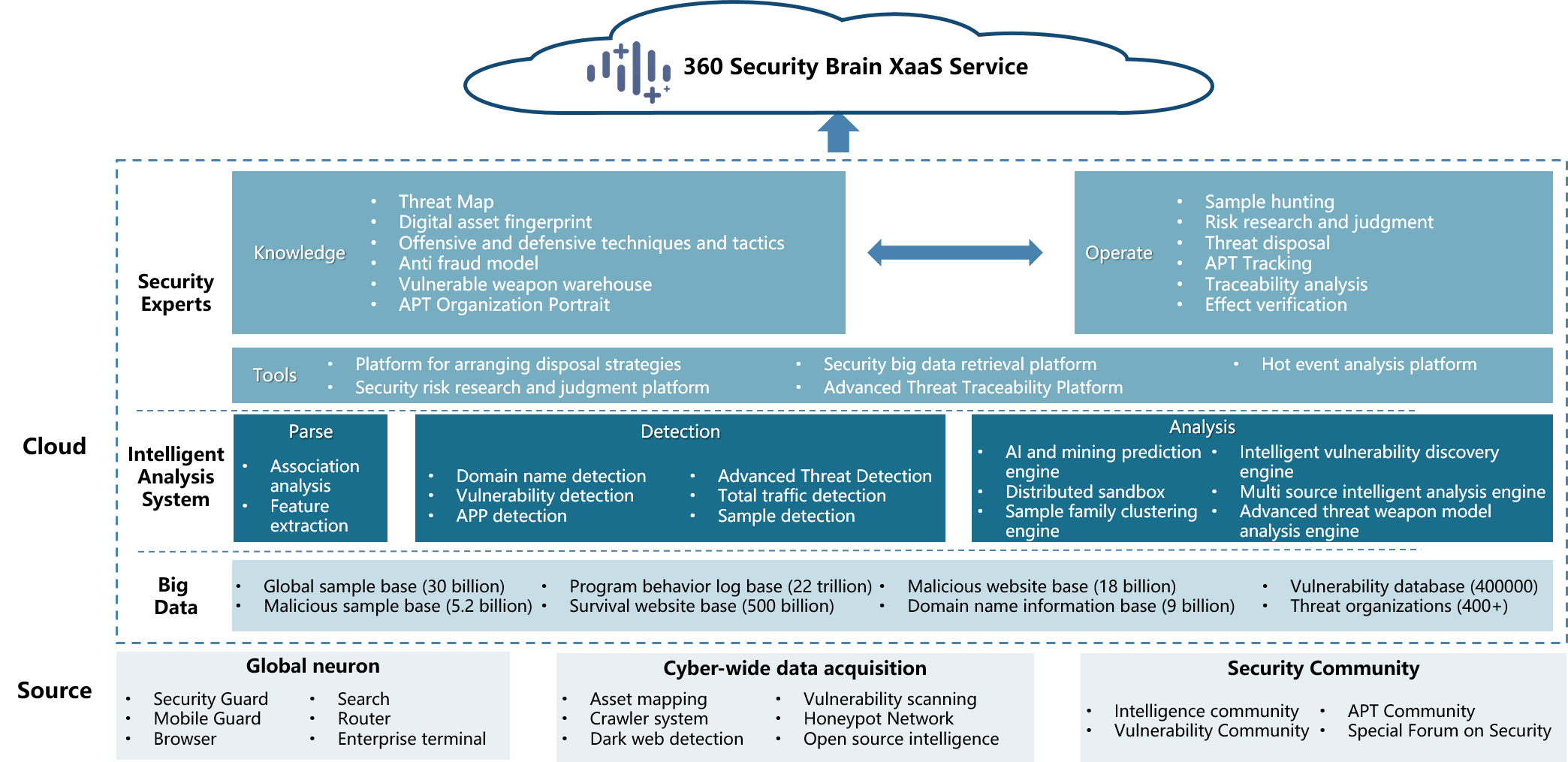
Specifically, the core of 360 Cyber-Wide Digital Security Brain system is divided into three layers. The first layer is the security big data platform, the second layer is the intelligent analysis and detection platform, and the third layer is the expert operation platform. In this way, the cyber-wide big data can be gathered, analyzed, and processed to form an insight into security threats. Finally, through external XaaS cloud services, users can see threats and provide targeted action guidance.
At the data layer, 360 has protected network security for hundreds of millions of Internet users in the past 17 years. On average, it has responded to 650 thousand file queries every second, intercepted 40 thousand malicious Web sites, had more than 30 billion samples, had more than 2,000 PB of data, and added 1,500 TB of data every day. While accumulating data, it has also established a huge website database, domain name database, vulnerability database, virus behavior database, mapping asset database, national threat organization information database, etc., and linked them together to form the world's largest security big data platform.
At the layer of intelligent analysis and detection platform, 360 has developed the world's first anti-virus and advanced threat detection intelligent analysis engine using AI technology, and gradually developed into a comprehensive intelligent analysis system. Several 360 engines have been integrated in intelligent analysis, research and identification. A special technical team maintains the feature rules necessary for detection and recognition, and releases the latest recognition feature rules to the rule base at any time, For any new sample, on average, all its features can be extracted at the second level and matched with these attack activity feature databases to determine which attack organization it belongs to and which attack means it adopts.
At the expert operation layer, in the past ten years, 360 has established a threat map for each attack, which is also a core asset of 360. It is accumulated bit by bit through the analysis of each APT attack and the summary of each attack and defense drill.
360 combines big data technology with artificial intelligence technologies such as feature engineering, graph analysis and knowledge reasoning, and applies it to the world's largest threat map formed in the security field, which is composed of 10 billion vertices and 100 billion edges. Through the threat map, all data related to attack and defense, such as IP, samples, web addresses, domain names, certificates and behaviors, can be extracted with their key features through feature engineering. These features are linked by graph analysis, and then knowledge reasoning is carried out based on the correlation of these features to locate the attack organization.
Comprehensive Practice from Country and City to Enterprises and Individuals
At the national level, based on 360 cyber-wide digital security brain, 360 has captured 50 overseas APT organizations, collected and mastered threat intelligence from more than 400 organizations around the world, obtained more than 20 thousand APT threat samples, built 1.5 thousand APT gene banks and detection models, and formed an APT knowledge map of offensive and defensive confrontation. At the same time, it has detected more than 5,200 high-level network attacks against important institutions and units so far in China.
At the city level, 360 cyber-wide digital security brain has also successively served the operation of urban digital security based in Chongqing, Tianjin, Qingdao, Hebi, Suzhou, Zhengzhou, Shanghai, Zhoukou and other cities, setting a landmark example of city level security services.
Taking 360 Chongqing Hechuan Digital Security Base as an example, at present, the city security brain has conducted centralized monitoring and management on the business scenarios of data resource management departments at the urban level in Chongqing, as well as nearly 100 units such as the government, enterprises, operators, education, medical care, and electric power. It has found 1,803,394 security incidents such as virus blackmail, Web attacks, phishing, and 10,036 security vulnerabilities. Through the way of security situation awareness, notification and disposal, it has assisted in the safety rectification of more than 100 high-risk risks, and effectively improved the safety protection awareness and protection capability of the supervised units.
At the enterprise and individual level, 360 Cyber-Wide Digital Security Brain processes 56 billion cloud searches, intercepts 750 million malicious websites, protects 10 million extortion attacks, and intercepts more than 20 million mobile malicious fraud attacks every day, providing reliable and stable security cloud services for 1.5 billion end users worldwide in 17 years.
"Seeing" Digital Security Risks, Escorting the Development of Digital Economy
Based on the 360 Cyber-Wide Digital Security Brain, 360 focuses on solving the problem of "invisible" threats to digital security. At the same time, it replicates the digital security capabilities to cities and industries, including the free output of SaaS model to small, medium and micro enterprises, accelerating the digital development of industries, and providing key support for the rapid development of the digital economy.
Medical is an important industry in the field of public services. Taking the General Hospital of Tianjin Medical University as an example, 360 has helped it build a dynamic security operation service system with the Cyber-Wide Digital Security Brain as the core. Covering 300+ intranet servers and 3000+ terminals in the general hospital, it has access to nearly 32 billion kinds of security data. It has helped the general hospital to realize the discovery of advanced persistent threats, early warning of security events, awareness of security situations, analysis of threat intelligence, traceability of attack behaviors, and output a full range of data, experts, AI, services and operation capabilities, realizing the global situation awareness, dynamic comprehensive protection, and continuous safe operation to fully ensure the safe operation of the Internet+ medical business of the general hospital, continue to improve the security protection capability, effectively ensure the safe and stable operation of all business systems, and establish the Internet+ medical security operation benchmark.


 联系我们
联系我们


